This piece was originally published at Revue on March 17, 2022.
Dear Watchers of US-China Relations:
To those who signed up recently, welcome to Wei To Think Again. This is my newsletter for the folks seeking to understand the nuances of US-China relations. If you haven’t done so already, please sign up here. If you have, help us grow by forwarding the letter to a friend.
Like many of you, I’m following the Russian invasion of Ukraine, and I came across an interesting thread of open-source intelligence stories that I’d like to share with you. We’ll get back to the Huawei series after this.
An Open-Source Intelligence Event
First, I’m thrilled to announce that I’ll be doing a Twitter Spaces event sometime in the next couple weeks with my Mercatus colleague Martin Gurri, a former Central Intelligence Agency analyst who writes prolifically about the relationship between politics and global media, including his 2014 book The Revolt of the Public.
We’ll chat about open-source intelligence (OSINT)—not just the recent developments in the Ukraine war but also propaganda analysis, which Martin had worked on in the Agency for years and which the Policy Change Index project I lead is all about. So follow us on Twitter and keep an eye out for the event so you can tune in!
OSINT Can Empower... Our Adversaries
At the beginning of World War II, Germany was dropping its newly developed electrical bombs on the United Kingdom. Some did not explode, and hundreds of Royal Engineers lost their lives because they tried but failed to defuse them. Granted, the British Army was just setting up its bomb disposal teams then, so the house was not exactly in order.
But here’s a surprising bit: Years prior to that, in 1932, the key technology behind such bombs, called the ECR (Electrical, Condenser, Resistance) fuse, had already been entered into the public records of the British patent office. In the words of retired Army Maj. John Davis, who recounted the story in ARMY Magazine, those brave men died “while the answer they sought gathered dust in an unlikely place.“
Here’s an even more surprising bit: The inventor of the ECR fuse was an engineer named Hubert Ruhlemann, who worked for Rheinmetall, a German arms manufacturer. According to James Owen’s book Danger UXB: The Heroic Story of the WWII Bomb Disposal Teams, Rheinmetall tested those electrical bombs in the USSR in the early 1930s and subsequently took out 85 patents on a range of bomb fuses before World War II broke out.
So, Britain’s overlooking OSINT—the approach to intelligence using publicly available information—means that hundreds of lives could have been saved, at minimum. But much more than that, what if our adversaries paid more attention to the open sources in our domain than we did?
Russia's OSINT Is Behind—For Now
I often write about how China values OSINT more than Western countries do. Apparently, so did the Soviet Union. The Federal Bureau of Investigation estimated that up to 90 percent of the information obtained by the Soviets came from open sources. But how about Vladimir Putin’s Russia, the free world’s loudest adversary right now? That’s harder to say.
Remember the ring of deep-cover Russian agents exposed in the United States by the FBI in 2010? Those spies, called “illegals,” were operating at a high cost to the Kremlin because they had to assume and build up convincing, false identities in America for a substantial period of time. (The event even inspired the popular FX television series “The Americans.”)
But here’s the interesting bit: For all the trouble sending them to America, Moscow assigned them to nose around in U.S. think tanks. As someone who has worked in those places, I often get my “intelligence” on my colleagues’ “agendas” simply by browsing our organization’s website. One of those Russian “illegals,” Evgeny Buryakov, was tasked with assessing the impact of economic sanctions on Russia, and he fulfilled the assignment by—you got it—searching the internet.
Many have noted the surprising Russian blunder in its current invasion of Ukraine: flawed planning, overly optimistic projection of victory, poor maintenance, and more. But perhaps that shouldn’t have been a surprise given how archaic the Kremlin’s understanding of OSINT was.
Russian Big Tech's OSINT Capabilities
But will Moscow’s OSINT sloppiness last? Not necessarily. The Kremlin’s intelligence apparatus may be behind the times with open sources, but Russia’s technology companies are not, and it may be only a matter of time before those firms use their OSINT capabilities to serve Big Brother, just like their Chinese counterparts do.
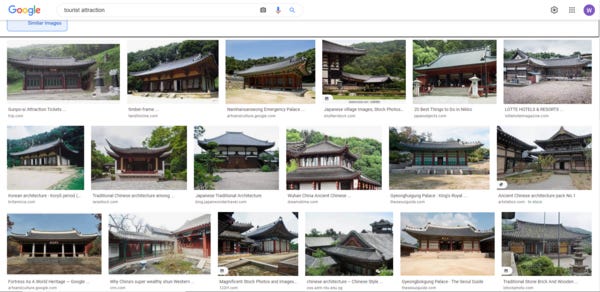
I did a quick test of Russia’s OSINT potential. Consider the photo below, which I took in a trip to North Korea—yes, I went, and yes, I took a lot of photos that I wasn’t allowed to, but that’s a story for another time. Image that you come across this image and want to geolocate those temples; that’s similar to how OSINT analysts examine images these days to learn about Russian troop movements in Ukraine. (The right answer is that they are located in a mountain called Pohyonsa.)
You might think that an image search on Google would return other people’s photos of the same site, which would then tell you where this place is. I tried that, and while Google did pick out similar temples, all the search results were sites in China, South Korea, or Japan. So, none got it right.
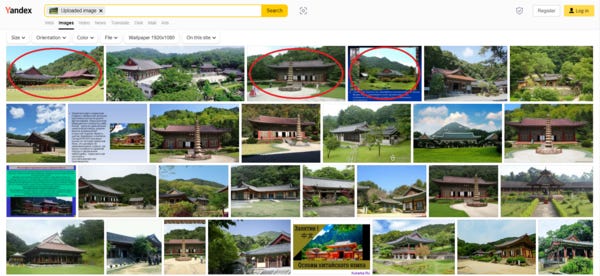
Then, I tried Yandex, the Russian equivalent of Google. Not only did many of the results match the actual site in North Korea (including three of the first four!), but the search engine even found several images of a tower at Pohyonsa that’s not in my original photo. (See the third one in the first row, as well as several elsewhere.)
It’s no wonder that Yandex has overtaken Google as Russia’s top search engine since 2018. Moscow’s intelligence posture may take a big leap forward if Russian companies and individuals support their government like the free world now roots for Ukraine.
Western intelligence agencies apparently are aware of Russian Big Tech’s potentials; they were poking around in Yandex in 2018 trying to hack its user accounts. But that’s a wrong lesson learned. The future of intelligence lies in the open, not in the dark.
Contact Me
Forward this to a friend, contact me with feedback, or both!